What is employee self-service (ESS)?
Employee self-service (ESS) is a widely used human resources technology that enables employees to perform many job-related functions that were once largely paper-based, or otherwise maintained by management, administrative or human resources (HR) staff.
ESS tools enable employees to handle many tasks relevant to their employment. By logging into the company's ESS portal, they can apply for reimbursement, request leave, download salary slips, keep track of hours/days worked, access courses and update personal information. They can also access company information relevant to their role or workplace experience, including benefits, surveys and work schedules.
Employee self-service is often available through the employer's intranet or portal. It can also be part of larger human capital management (HCM), human resource management (HRM) system, human resource information system (HRIS), enterprise resource planning (ERP) or benefits administration software, which is often delivered via SaaS platforms.
The acronym ESS is not used as widely as it was when the technology first became prevalent in the early 2000s. Now, self-service features are considered basic functionality in most big HCM, HRM or HRIS systems.
Benefits of employee self-service
ESS portals empower employees to self-manage many aspects of their employment. By giving workers direct control over their employment information plus autonomy to manage their benefits and payroll configurations, ESS technology helps create a positive work culture and retain talent -- particularly in an increasingly competitive talent market. These systems can also help make employees feel more connected to the organizations and, possibly, happier in their jobs and more productive.
Modern ESS systems are optimized for mobile or incorporated into companies' social media pages, making them easy to use and access at any time and from any authorized device with an internet connection. Easy accessibility to important information is a particularly useful feature for geographically dispersed teams, employees who work from home, and employees who travel frequently.
Employee self-service systems are often part of larger employee engagement strategies, which can include wellness programs, recognition, learning management systems and organization-wide social activities, all of which enable organizations to nurture talent and enhance the employee experiences (EX).
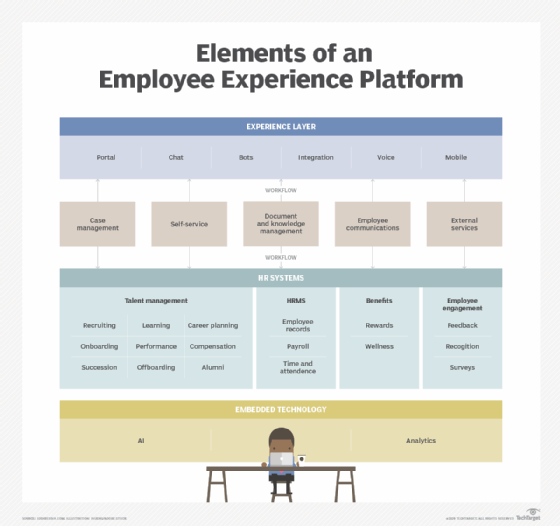
ESS can also improve the relationship between employees and management. It streamlines performance review processes and makes it easy to send wellness surveys to employees. In addition, these systems simplify timekeeping and scheduling, as well as minimize the potential for conflict between employees or between employees and management. Furthermore, training programs can be integrated into the ESS tool to encourage employees to keep learning and take charge of their own career trajectories.
ESS also streamlines many processes in HR, payroll, employee engagement, and learning and development. It allows the staff in these departments to quickly access information, often improving job performance and motivation.
Key features of HR self-service software
Modern employee self-service software is usually incorporated into comprehensive HR technology systems and includes ESS features, which include the following:
- Payroll capabilities, such as online access to pay stubs, the ability to change tax withholding and deduction amounts, apply for leave, and log work time and hours.
- The ability for HR and other departments to shop for and choose benefit programs and manage open enrollment and other changes, such as major life events.
- The ability for employees to enroll in benefits, select or change insurance plans, and enroll in training programs.
- The ability for HR and other departments to make changes to retirement investment plans, such as changing employee contributions, setting up loans and making withdrawals.
- Employee onboarding.
- Integration with company timeclocks and the ability to create timekeeping logs, track employee time-off, and track leave and holidays.
- Built-in and customizable employee wellness surveys.
- Performance management forms and documents.
- Expense management.
- Business travel management.
Challenges of employee self-service
Integrating multiple employee self-service channels -- such as intranet, portal, wellness program apps and retirement accounts -- can be technologically difficult because of differing data formats and login procedures. Furthermore, managing the various configurations, logins, data sources and integrations might require additional IT effort, which smaller companies typically cannot spare.
Also, educating employees about self-service system capabilities and encouraging employees to use them can be a long process. Resistance to change and poor digital literacy can also hinder ESS adoption and use.
In addition, upgrading from legacy self-service systems to new ones can involve difficult decisions, such as budgeting, vendor selection, essential features and required integrations. Other concerns might involve whether systems from disparate vendors are compatible or whether to replace a stand-alone self-service system with a specialized module from an HCM, ERP or benefits software vendor.
Concerns around system maintenance and compliance might also arise. Regular maintenance might be required to take data backups, minimize login problems, simplify upgrades and patching, and prevent system crashes. If the vendor cannot -- or will not -- take care of these activities, it can increase the burden on internal staff. It can also be difficult to ensure that all the information within the system is compliant with relevant data privacy laws. Noncompliance can result in punitive action from regulators, including fines and legal action.
Learn the pros and cons of some top vendors and tools and get buying tips to ensure your purchase is a success by exploring top HR software and tool options to consider. Also, check out the most impactful employee experience apps.







