
pogonici - Fotolia
How to protect backups from ransomware infiltration
Your ransomware backup protection strategy needs to address advanced persistent threats that encrypt files over time. Learn how to restore backups to avoid a payout.
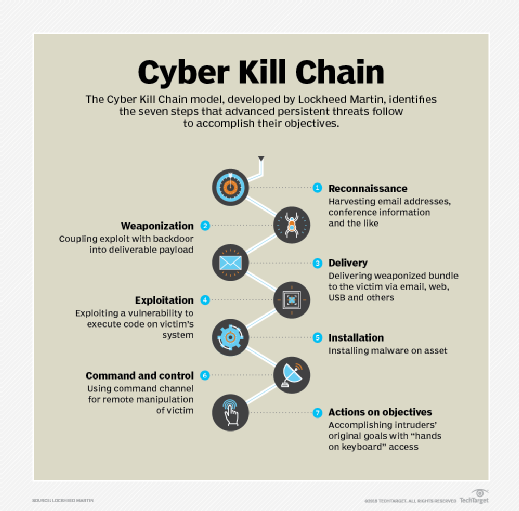
There has been a tactical pivot in ransomware. It seems that ransomware writers have realized that large organizations have lots of money, and some do not have the best protection against infections. Newer ransomware is behaving as an advanced persistent threat, a piece of malware that tries to stay undetected in your network for some time to do the maximum amount of damage.
The APT will usually spread through your network, infecting as many computers as possible. Often, the malware will try to connect to a command-and-control server over the internet to report the progress of the infection and await the command to attack. To respond to this new threat, you need different approaches to protect backups from ransomware.
Beware your restore
A ransomware APT attack may start by stealthily spreading itself through your network and infecting all of your computers. It will then seek out file-based backups and valuable but older files to encrypt. The aim is to get as much of your infrastructure infected and encrypted -- over a period of weeks or months -- before you are alerted and can protect backups from ransomware. By slowly encrypting files, the ransomware is making the process of recovering from backups slow and expensive, perhaps more costly than paying the ransom. Once the infection is complete, and your backups contain a mix of encrypted and clean files, then it is time to detonate the ransomware. All of the infected machines will suddenly encrypt recently used files, and your applications will stop working.
Because the APT ransomware has been in the network for weeks before it detonates, it probably has been backed up numerous times. Your backups now contain both encrypted files and the ransomware application itself. If you bulk restore whole systems in an attempt to protect backups from ransomware, you will also restore the infection and negate all of the cleanup work you have already completed. Be very cautious about restoring any executable files, scripts such as JavaScript or even files that may contain macros until you know how the ransomware spreads. Ideally, you only want to restore data files.
Analytics to the rescue
You probably have thousands of encrypted files, and with the last unencrypted versions spread across multiple backups, you'll need to work out what to restore. Your backup application should use its backup catalogs to identify the last unencrypted version of each file and automatically restore those versions. If those backups are to tape, it will take a while to work through each tape. If the backups are to disk, it should take less time to recover.
Backups should not be accessible as files over the network, as they will be prime targets for encryption by the ransomware first. If your backup application can identify encrypted files, it might be the thing in your network to identify a ransomware infection. One sure sign of the presence of ransomware is the need to back up a lot of non-compressible files in a directory that previously only contained compressible files.
Ransomware has evolved and is targeting enterprises by behaving as an advanced persistent threat. You need to be aware of these changes and protect backups from ransomware by identifying the infection rapidly and recovering without paying a ransom.








